AEM like most of the web applications can be subject to multiple vulnerabilities.
The most common vulnerabilities and attack vectors are summarized by the OWASP project.
To protect AEM from external attacks the most important place where blocking/ filtering rules should be implemented is the Dispatcher.
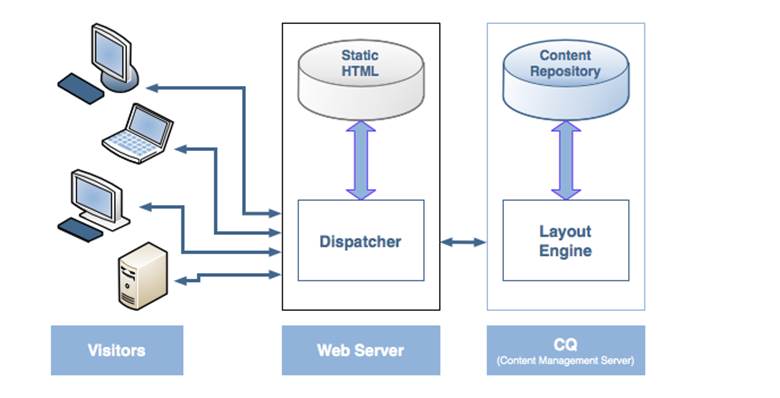
The dispatcher is all external visitor entry point where filters should be implemented.
Here are some detailed notes on securing dispatcher.
A good starting point is to use production ready mode for all production instances.
This mode disables most of the unsecure and unneeded components.
It is also important to be sure that the dispatcher security checklist has been implemented.
The checklist, for example, states that most of filters (selectors, query strings, etc…) should deny by default and only whitelist what is really needed.
While setting up the whitelisting be very careful on what you are exposing.
Consider to follow these rules of the thumb:
- Always expose only what you
really need, ie /content/yoursite rather than /content - Be careful exposing extensions
and prefer to do only where make it sense, ie if you have images only in the
dam consider to open image extentions only in /content/dam/your site rather
that simply allow *.gif and similar everywhere. - The same thing about selectors
and suffixes, but more strict. Allow selectors and suffix only where you need
according to the architecture of your site. - The rule are validated
serially, so pay attention to not reopen something you have closed before.
Finally, it is important to check for hotfixes and patches of serious vulnerabilities and apply or mitigate as soon as possible.
XSS prevention
XSS (cross site scripting) allows inclusion of untrusted data in the page.
In the past a large number of known AEM vulnerabilities ( CVE ) were of this type.
The XSS protection mechanism provided by AEM is based on the AntiSamy Java Library
Also using HTL can prevent XSS
CSFR
Cross site request forgery can be prevented by using token.json.
public available useful ‘hacking’ tools
These tools scan for known vulnerabilities, default users and passwords and other common possible misconfigurations.
Aem hacker
python3 scripts , requires port 443 reachable on internet from scanning IP
source https://github.com/0ang3el/aem-hacker
python aem_hacker.py -u https://mydomain --host myscanningip
[+] New Finding!!!
Name: CRXDE Lite/CRX
Url: https://mydomain/crx/explorer/browser/index.jsp
Description: Sensitive information might be exposed. Check manually.
[+] New Finding!!!
Name: WebDAV exposed
Url: https://mydomain/crx/repository/test
Description: WebDAV might we vulnerable to CVE-2015-1833. Check it manually. See - http://mail-archives.apache.org/mod_mbox/jackrabbit-announce/201505.mbox/raw/%3C555DA644.8080908@greenbytes
.de%3E/3Aemscan
another python 2 tool
source https://github.com/Raz0r/aemscan
./aemscan https://mydomain.com
______ __ __ _____
/\ | ____| \/ |/ ____|
/ \ | |__ | \ / | (___ ___ __ _ _ __
/ /\ \ | __| | |\/| |\___ \ / __/ _` | '_
/ ____ \| |____| | | |____) | (_| (_| | | | |
/_/ \_\______|_| |_|_____/ \___\__,_|_| |_|
aemscan - Adobe Experience Manager Vulnerability Scanner
version: 1.0
Cannot get AEM version
Custom error pages are enabled
WebDAV is enabled
Scanning useful paths [####################################] 100%
Found 1 paths:
/system/sling/cqform/defaultlogin.html
AEM authentication is available
Checking default credentials [####################################] 100%Written by Andrea Berger and Alessandro Paolinelli




